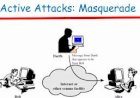
Security mechanisms in a computer system
Security mechanisms are strategies set by organisation to address issue of computer system security, these protocols are set by organisation so to prevent unauthorised access by to their private data and files.

Introduction
Security mechanisms are strategies set by organisation to address issue of computer system security, these protocols are set by organisation so to prevent unauthorised access by to their private data and files.For success of an organisation it should implement a good protocol of securing their data so to avoid their rivals from accessing confidential information. Below are some of security mechanisms
READ ALSO: Hackers Steals Hundreds Of Millions Of iPhones Data Which Apple Can't Stop.
1.0 Encipherment it used to protect confidential data and also infromation flow. Encipherment can be done through encryption techniques.
2.0 Digital signatures are used to provide analog signature to electronic system.So long as one need to access the system he/she should not forgot the signature. Incase user forgot to enter the exact signature the system will not open.
3.0 Access control mechanisms this senario of access control ensures that only authorised user can access the system. It is used to deter the unauthorised user since before login you need to give the system certain credentilas which incase they don't match the sytem would allow to access the information.
READ ALSO: Type of hackers and common tools they use
4.0 Data integrity mechanism data integrity technique is used to protect the integrity of the data, it is used to ensure that data in transit is not tempered with by hackers.
5.0 authentication mechanism systems are designed such that it only authenticate user before allowing them to access the system.
6.0 Traffic padding used to prevent attack through traffic analysis traffic padding can be effective if they are protected well.
7.0 Routing control used to choose dynamically data routes on transit here communication systems are used to detect passive or active data attacks.
8.0 Notarization mechanisms used to ensure certain properties of data communicated between two or more entities such as origin,identity and destination of that data.
9.0 physical security this is achieved by ensuring computer systems are kept in a secure place, the place should be equipped with strong doors with indoor locks so to prevent intruder from physcically accessing the resources.
10.0 Auditing refers to process of recording and checking events to detect wether unauthorised activity has occured or an attempt
READ ALSO: Types of computer viruses
#Security Think Tank: UTM attractive to SMEs, but beware potential pitfalls via @maxineholt https://t.co/urk0lu5fld pic.twitter.com/Qc5Mxv1sx1
— TenisiTech (@TenisiTech) December 17, 2019
Wow, select #Helsinki buses now have free USB charging ports! Not sure if I feel secure enough to plug my phone in.. #security pic.twitter.com/Z9pn0r0Xqu
— Jussi Roine (@JussiRoine) December 17, 2019
Web Tools for Pentesters and Security Researchers:
— trimstray (@trimstray) December 17, 2019
» SSL/Security
» HTTP Headers & Web Linters
» DNS & Mail
» Net-Tools
» Privacy
» Performance
» Code Parsers
» Passwords
» CVE/Exploits
▸ https://t.co/37le6OIHGh#IT #tech #news #Security #infosec #CyberSecurity #ITsecurity pic.twitter.com/atbMq278Lx
My new post about how to NOT manage a #bugbounty program #securityhttps://t.co/MCVWSWKwyS
— Gwendal Le Coguic (@gwendallecoguic) December 17, 2019
SUBSCRIBE TO OUR YOUTUBE CHANNEL BELOW TO WATCH MORE VIDEOS