Most common cloud computing security issues
Efficiency, affordability and scalability are features which should be accompanied by cloud computing although if proper solutions not adapted it may lead to vulrnerability.

Efficiency, affordability and scalability are features which should be accompanied by cloud computing although if proper solutions not adapted it may lead to vulrnerability. Security issues remain one of major concern in cloud computing since no organisation will easily hand offer their data to the other organisation. Here are most cloud computing security issues.
READ ALSO: Advantages and disadvantages of V-Model
1.0 Distributed denial of service.
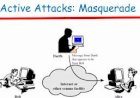
When cloud computing came in service distributed denial of service became unthinkable element. Distributed denial of service has greatly increased in cloud computing. If great traffic is initiated in the cloud computing it may result in low performance and system start to run slow.
2.0 Shared computing services.
In multi-tenant access of service it may lead to increased sharing of service which in turn may lead to increased traffic.Similarly if attack is meant to one user it may alternatively affect all other users hence this making sharing of computer resources are risk.
READ ALSO: Database Management System
3.0 Employee negligence
employees negligence and mistake remains one of the most issues in cloud computing,employees may log into the system and forgot to log out to the system. This may attract unauthorised user to come and access the senstitive information and cause more harm.
4.0 Data loss and inadequate data backups
Data loss and inadequate data backups has remained one of biggest challenge affecting cloud computing. Hackers may target organisation and delete all organisational data, this wil lead to data loss hence negatively affect the organisation.
READ ALSO: How to Create Android Horizontal Scrolling RecyclerView
5.0 Phishing and social engineering attacks
Phishing and social engineering attacks has came common due to openness of cloud computing. Users should be aware of phishing and social engineering attacks so as to avoid these types of attacks.
6.0 System vulnerabilities
Cloud computing may contain some vulnerabilities especially if the network has a complex infrastructure or complexities.If the vulnerability is known by the hacker he may utilise it so as to negatively affect the organisation
7.0 Costing model Cloud computing may come up with additional cost which may include cost of data communication, data transfering and also other costs. These cost may seem to be burden to the organisation hence become issues to cloud computing.
READ ALSO: SOFTWARE DEVELOPMENT LIFE CYCLE MODELS
10 ways #AI is becoming more #Autonomos and #Inventive > #PwC via @MikeQuindazzi
— Skytel Teleservices Pvt Ltd (@skytel_social) December 12, 2019
> #IoT #SaaS #CloudComputing #DataAnalytics #Robotics > #FutureofWork pic.twitter.com/3I1MbiFOdO
Firms believe hybrid or private cloud to be the future, research shows. #cloudcomputing #avayanation https://t.co/unAXKfyQxu pic.twitter.com/bYHBnnBSGJ
— Stacey Terrazas (@smterrazas78) December 18, 2019
Screen-locking is a great way to keep your #data secure.
— IT-Works ????️ (@IT_Works2012) December 16, 2019
Most computers lock or sleep after several minutes of being inactive but in order to ensure maximum security you should set a limited timer.
More #DataSecurity tips here... https://t.co/uzJjC0lWBw #WorcestershireHour pic.twitter.com/15gFLwkeNo
How safe is your Gmail account? Are you sure you’ve done enough to safeguard it? If you have even a tiny doubt, check out these tips and ensure your data is safe. #DataSecurity #Gmail https://t.co/U8DMe7aMxI
— Hiver (@hiverhq) December 18, 2019
SUBSCRIBE TO OUR YOUTUBE CHANNEL BELOW TO WATCH MORE VIDEOS