Types of encryption which are most secure
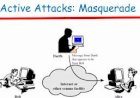
Encryption is process of translating data into another form so that people with secret key are only one to access the data.

Encryption is process of translating data into another form so that people with secret key are only one to access the data. Encrypted data is reffered to as ciphertext whereas unencrypted data is reffered as plaintext. Currently encryption is one of most secure and best process in the organisation. Two main encryption process include symmetric and asymmetric.Basic purpose of data encryption is to ensure confidentiality of the data on transit.
READ ALSO: Hackers Steals Hundreds Of Millions Of iPhones Data Which Apple Can't Stop.
Types of encryption
a.triple DES triple DES has been designed so as to replace standard encryption standard alogirthm.The triple DES normally use three keys with 56 keys each.Triple DES is widely used to manage hardware encryption
b.RSA is a public encryption and also standard encryption algorithm for encrpting data sent over internet.RSA is considered to be asymmetric algorithm because it uses pair of keys. You use public key to encrypt data and also private key to decrypt the message, Hence this makes hackers to take time before hacking the message.
READ ALSO: Security mechanisms in a computer system
c.Blowfish is another algorithm designed to replace DES, the symmetric cipher breaks the message into 64 bits and encrypt each message individually, blowfish are found in range of softwares that can be applied in e-commerce to encrypt payment systems etc
d.Twofish Bruce Schneier a computer expert is mastermind behind the invention of blowfish invention. Key used may add upto 256 bits length , blowfish is one of fastest kind of encryption algorithm,Blowfish can be used in both hardware and software setup.
e.AES It is standard algorithm trusted by many organisations across the world. AES can use 192 bits and 252 bits keys for heavy encryption. AES is considered best for encryption due to fact it is considered in many private sectors.
READ ALSO: Type of hackers and common tools they use

Encryption is conversion of a standard message in plain text to an unreadable format that can only be decoded by the owner of the message and whoever they send it to. Click on the link to find out morehttps://t.co/TC2CddGTT3#CyberSec #encryption pic.twitter.com/ueeQR9sfU4
— MediasTube (@mediastube_) December 17, 2019
#encryption can protect a bad guy... it also protects millions of people who rely on strong encryption to protect them from tyrannical governments.
— Craig Beebe (@cabeebe100) December 17, 2019
Not fearing your government is a relatively new experience in human history, don’t take it for granted. https://t.co/rhcUK9QAJb
The new domain name getencrypted .com has been listed for sale at https://t.co/XvOAtXCrKl , buy it before its gone! click here: https://t.co/tUBjnlws5U #Eten #Encrypt #Getencrypted
— Perfectdomain.com (@perfectdomain1) December 16, 2019
Most public #WiFi hotspots are not secure and do not #encrypt information sent over the internet, so you need to be careful! Check out more tips: https://t.co/qzLWWTDvqo pic.twitter.com/T3fAvhzJJK
— Prelude Services (@PreludeServices) December 14, 2019
We make public WIFI safer????????????
— HelloVPN (@VpnHello) December 13, 2019
Hackers can’t access your private information as the connection is secured???? ???? ???? #online #Internet #protect #encrypt #Browser #Google #tech #Chrome #web #free #blog #surveillance #data pic.twitter.com/FXyP4KdqKe
While #Encrypted, #OpenSource research indicates numerous techniques available to passively view the video and metadata from the #AirVehicle as well as assume control over the air vehicle by #Adversaries #DroneSecurity #DroneHacking https://t.co/erEoPZtSQm
— Taslet Security (@TasletCom) December 17, 2019
❄️ ⛄ ???? ‘Tis the season to send holiday cards and annual updates to family and friends! Read our latest article on how to send messages privately. What encrypted messaging services do you use? https://t.co/xU4En96IKz #privacy #encrypted #encryption #datarights #startpage pic.twitter.com/FUii0MLdTN
— Startpage (@startpage) December 10, 2019
SUBSCRIBE TO OUR YOUTUBE CHANNEL BELOW TO WATCH MORE VIDEOS