This website uses cookies. By using this website you consent to our use of these cookies.
Technologies
wifi network, advantages and disadvantages
This is a wireless network that connects the router which supplies the network to...
email, advantages and disadvanatages
This is the process by which people exchange messages from one network to another...
Applications of NOSQL database
Technology has advanced, and as a result most of the activities that occur day to...
SQL, advantages and disadvantages
SQL is a programming language that is designed for the purpose of managing data...
SQL applications
SQL is used as a client server language which links front end to back end and as...
how to maintain data integrity
Data integrity is the process of ensuring that data is only accessed and that modification...
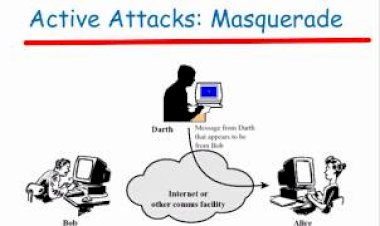
Masquerade Attacks
This is a type of attack where intruders presents themselves as an authorized entity...
Ways of preventing data security breach
The term breach of data security refers to the process by which data or information...
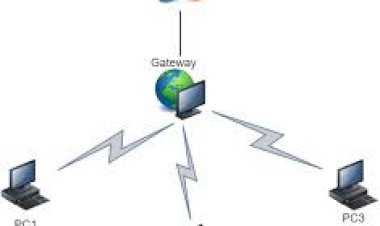
gateway, advantages and disadvantages
Two or more computers are able to communicate to each other through an established...
Challenges Facing E-commerce.
Shopping platforms have eliminated many barriers of entry. Anybody can launch...
The advantages and disadvantages of Internet Of Things
Internet of things is influencing our day-to-day objects with machine-readable...
Ethical Challenges of Information Technology
With tools like the internet access, hackers have found it easy to hack into any...
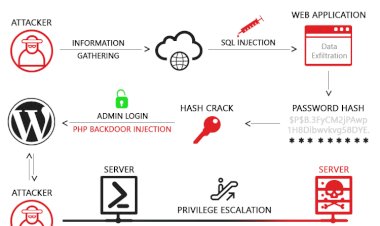
Types of cyber-crime.
Occurs when a cyber-criminals impersonate person else identity to practice malfunction....
How banks are using internet of things
It is fair to say that most of banks haven’t really got into the wave of the IoT...
cryptographic techniques
Encryption is the process by which data or information is encoded in a way that...