Masquerade Attacks
This is a type of attack where intruders presents themselves as an authorized entity in order to gain access to user data. They mostly occur in the form of intruders gaining access to user passwords and login details.

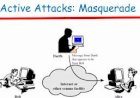
MASQUERADE ATTACKS
This is a type of attack where intruders presents themselves as an authorized entity in order to gain access to user data. They mostly occur in the form of intruders gaining access to user passwords and login details. An employee working in an organization can be able to conduct the masquerade attack by using a colleagues login details to access some data he or she is not authorized to access or an outside intruder who uses the network to gain unauthorized access. It can also happen that an insider can help an outside intruder gain access to an employee data. Masquerade attack is a type of impersonation since the intruder uses the identity of an authorized entity to gain access to data illegally.
DOWNLOAD ALSO: Customer Relationship Management System
Ways of preventing masquerade attacks.
- People should formulate a precaution measure of changing of passwords occasionally in order to minimize the risk of the password being hacked and used to access the users data. The users of the website or a certain android applications should also select a password that they have not used before.
- Users of a certain system should also ensure that once they have completed their work in their accounts, they should log out of the system so as to minimize the risk of access of their data.
DOWNLOAD ALSO: Online Exam Android App with Admin Panel
- The use of two factor authentication is being implemented in systems that store sensitive data as a means of curbing the masquerade attacks since the intruders will have a hard time knowing the two factor authentication of a user.
- System users during the creation and generation of passwords should also ensure that they create passwords that are long in that they contain many characters to minimize hacking.
- Intruders have a tactic that they commonly use to hack user data by sending emails to users and thereby tricking them to click the links in the emails. Employees or individuals should be educated to ignore emails sent to them by unknown people or from unknown sources.
DOWNLOAD ALSO: An E-Commerce Website with free Source Codes.
For more information. You can contact me @
Email –geeksourcecodes@gmail.com
Mobile No. – +254714643906
Or feel free to comment below.
SUBSCRIBE TO OUR YOUTUBE CHANNEL BELOW TO WATCH MORE VIDEOS