This website uses cookies. By using this website you consent to our use of these cookies.
Learn
How To Access Passwords for Wi-Fi Networks You've Connected...
With an Android Phone, You Must Have probably connected to dozens of Wi-Fi networks....
TCP/IP model advantages and disadvantages
It ensures that all the devices visit the internet are recognizable since it issues...
Types of e-commerce models and their advantages
Refers to commerce over the internet, the name is self explanatory since buyers...
TCP/IP MODEL
The term TCP/IP model refers to Transmission Control Protocol and Internet Protocol....
Network cabling
A cable is a physical equipment in which information flows from one device to another,...
Tips of how to market sales on instagram
Today social media are becoming hotcake incase one need to implement a marketing...
Management Information System
This is a collection of software and hardware designed to help in operation of activities...
Essential factors to consider while developing a website
Web development is not an easy task as many of people are forced to believe. It...
Types of topology
This is a term used to describe the physical layout or mapping of a network. Network...
Traditional file system
It included the use of physical files to store data and records. Organizations...
Database Management System
This is a system created to deal with the collection of data from a database that...
Biometrics authentication
The aim of Biometrics is to protect individuals and organizations from intrusion...
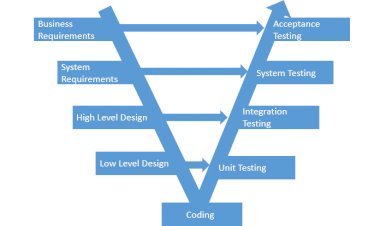
Advantages and disadvantages of V-Model
These are Summary of the Best Advantages and disadvantages of V-Model
What You MUST Know About System security
This is the process by which an entity secures its network and resources from access...