This website uses cookies. By using this website you consent to our use of these cookies.
Cybersecurity
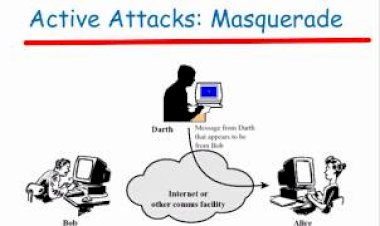
Masquerade Attacks
This is a type of attack where intruders presents themselves as an authorized entity...
Ethical Challenges of Information Technology
With tools like the internet access, hackers have found it easy to hack into any...
Characteristics and Effects of Virus on a Computer.
Computer virus share similar characteristics since they are designed by programmers...
Types of computer viruses
Computer virus refers to a malicious software that reproduces itself and replicates...
Type of hackers and common tools they use
Hacking is process of unauthorised intrusion to the computer system or a network,...
Security mechanisms in a computer system
Security mechanisms are strategies set by organisation to address issue of computer...
Top Types of cyber attacks
Types of cyber attacks 1.Phishing. This is the act by which fraudulent information...
Advantages of cyber security
Advantages of cyber security . 1.Protects developed systems from hacking. 2. Provides...
What you need to Know about Cyber security
This is the process of protecting and defending computer systems, servers, mobile...
Types of encryption which are most secure
Encryption is process of translating data into another form so that people with...
Hackers Steals Hundreds Of Millions Of iPhones Data Which...
“Apple cannot fix it because bootrom cannot be patched after a device leaves the...