Top Types of cyber attacks
Types of cyber attacks 1.Phishing. This is the act by which fraudulent information is sent to someone mainly in form of email with the aim of stealing sensitive information or data from a person or for them to install harmful softwares that cause virus to their machines.

Types of cyber attacks
1.Phishing.
This is the act by which fraudulent information is sent to someone mainly in form of email with the aim of stealing sensitive information or data from a person or for them to install harmful softwares that cause virus to their machines.
2. Denial of service attack.
The aim of denial of service attack is to ensure that network is unavailable to the users. This is done by causing traffic to the target which therefore crashes due to the traffic.
READ ALSO: Type of hackers and common tools they use
3. Injection attacks.
This is a type of attack that deals with injecting an application or website with data that causes harm to the application/website by obtaining data/information stored from the application.
4. Malware
This is a harmful software that causes virus to a system. This type of attack penetrates a network through a vulnerability such as when an end user clicks on a caertain link or email.Malware can alter how a system operates or functions and can also obtain information from hard drive of a computer system thereby breaching privacy of a user.
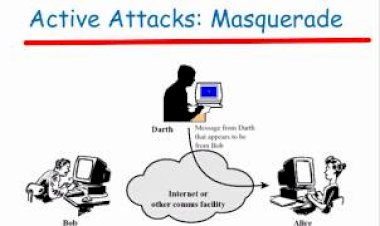
5.DNS spoofing.
This is a type of hacking which interferes with computer security. This type of attack leads traffic to the attackers system from where information will be accessed. It can go unnoticed for a long period of time and it also Interferes with end-users privacy.
READ ALSO: Hackers Steals Hundreds Of Millions Of iPhones Data Which Apple Can't Stop.
#NewOrleans Declares State Of Emergency After #CyberAttack#CISO #CyberSecurity
— Stéphane Chmielewski (@_SChmielewski) December 17, 2019
Cc: @robmay70 @NigelTozer @BillMew @archonsec @MHcommunicate @m49D4ch3lly @todddlyle @Fabriziobustama @sarbjeetjohal @psalvitti @DrJDrooghaag @ChuckDBrooks @mclynd @robmay70 https://t.co/ZlBUVWsCy9
Protecting the ‘Crown Jewels’ with Threat Hunting #CyberSec #infosec #Security #cybercrime #ThreatIntel #cyberattacks #fraud #cybersecurity #dataprotection #privacy #cyberthreats https://t.co/2PXy4GAMUF
— Jiniba (@JinibaBD) December 14, 2019
#Magecart attacks are some of the biggest threats to #ecommerce websites today. Unfamiliar? Check out a live attack in today’s PerimeterX webinar: https://t.co/VczaeI7H15 #eskimming #cyberattacks
— PerimeterX (@perimeterx) December 17, 2019
This is the latest #infographic that I did that shows the nine elements of the Digital Forensic Process ????????. Feel free to share ????, I hope it will be useful ???? #CyberSecurity#infosec #IoT #tech #ITsecurity CC @mikequindazzi #BigData #MachineLearning #AI #IoT #infographics mt: pic.twitter.com/sVYRfBkuWg
— Angela Wilson (@AngelHealthTech) December 17, 2019
A shift to rebrand the term #cybersecurity into the lexicon of business owners has brought about a new way of speaking to security issues.
— Archetype SC (@archetype_sc) December 16, 2019
Now, "risk management" is in use to portray the importance of security to businesses.
What do you prefer, cybersecurity or risk management? pic.twitter.com/jB492ETTqM
Malwarebytes: Join us for a webinar TODAY at 11am PT, where we'll reveal why healthcare #cybercrime is on the rise and how you can protect your organization. Sign up now:https://t.co/cv1Wwy8kyc pic.twitter.com/RqJX4G8eEI
— TheArea51Virtuoso (@Area51Virtuoso) December 17, 2019
New Orleans #Cyberattack still unexplained...! #Drill https://t.co/oOH1uhA7yA
— Dark Journalist (@darkjournalist) December 16, 2019
Retail #CyberAttack attempts up 20% last year https://t.co/3ZN2TiWGUs via @RetailDive #PCI
— Brian Pennington (@bfpennington) December 17, 2019
SUBSCRIBE TO OUR YOUTUBE CHANNEL BELOW TO WATCH MORE VIDEOS